OSEE Review - The Splendid Story of That Sophomore Summer
EXP-401 - Advanced Windows Exploitation
Background
About EXP-401 - Advanced Windows Exploitation / OSEE
EXP-401 - Advanced Windows Exploitation is positioned by OffSec as the highest-level exploit development course, and OSEE is the certification obtained after completing this course and passing a grueling 72-hour exam.
On the certification roadmap compiled by Paul Jerimy, it’s clear that OSEE is placed at the very top of all certifications and is recognized as one of the most difficult information security certifications in the world, therefore carrying extremely high value.
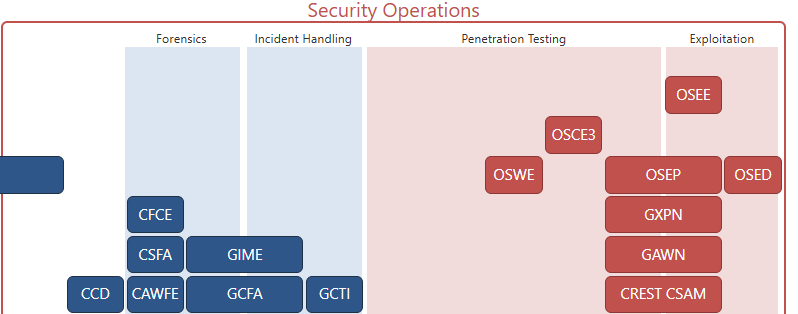 Paul Jerimy Security Certification Roadmap
Paul Jerimy Security Certification Roadmap
EXP-401 covers advanced exploitation techniques in User-Mode and Kernel-Mode in modern Windows systems, including:
- Bypassing modern User-Mode mitigations, such as DEP, ASLR, CFG, ACG, CET
- Bypassing modern Kernel-Mode mitigations, such as kASLR, NX, SMEP, SMAP, kCFG, HVCI
- Advanced Heap Manipulations to achieve Code Execution and Guest-To-Host as well as Sandbox Escapes
- Breaking WDEG defenses and establishing Version Independent to weaponize the exploit
- 64-bit Windows Kernel Reverse Engineering and vulnerability research
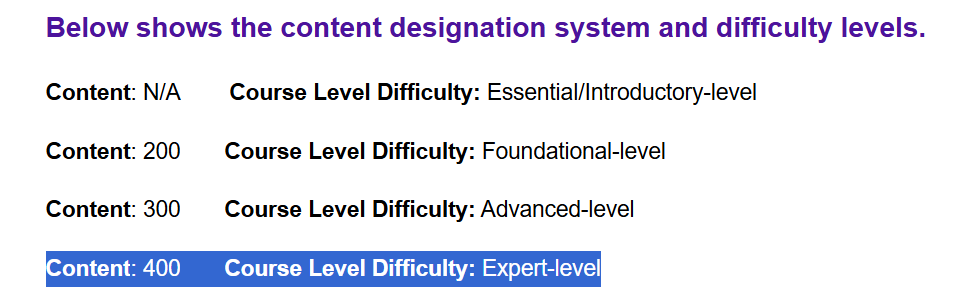
This is OffSec’s only 400-level course, corresponding to Expert-Level difficulty in the Course Code System. Honestly, just from the syllabus descriptions you can already imagine how difficult the course is.
Of course, the required prerequisites can’t be lacking either. Based on my own experience, to progress smoothly through the course you must have the following abilities:
- Basic IDA skills are sufficient; we didn’t use the Decompile feature at all, and even the Free version is fine
- Proficiency in using WinDbg for User-Mode and Kernel-Mode debugging
- Proficient shellcoding and ROP skills without these you won’t even survive the first day
- Various characteristics of the x86/64 architecture, such as calling conventions, paging mechanisms, register-related traits, etc.
- Proficient C / C++ programming skills, where “proficient” refers to low-level memory control
- Familiarity with common Win32 API functionalities and how to call them, especially calling them in a pwn-style way
- Familiarity with Windows Binary Exploitation techniques; it’s best to understand common vulnerability principles and corresponding exploitation methods
Among these, I think the most important is familiarity with WinDbg. In class, the instructor’s explanations were often at a highly abstract level. We were debugging an architecture under the assumption that we already understood WinDbg; commands flashed by with no reaction time. Usually, after understanding a concept, we would immediately and quickly inspect the underlying structures. If you can’t read WinDbg output, you’ll be left behind from the very morning of day one.
To be clear, this course is absolutely not suitable for beginners. Even if you aced OSED, you’ll still get utterly destroyed in EXP-401, especially in the Kernel-Mode portion. It’s best to have played with the following before the course starts:
HEVD helps immensely in building fundamentals for Windows Kernel exploitation. If you keep up with the latest trends in Windows Kernel exploitation and apply them to HEVD, you can even get a little ahead of some parts of EXP-401.
Connor McGarr’s blog is very helpful for User-Mode exploitation. If you want to prepare for User-Mode exploitation first, you can read it together with Windows x64 architecture materials. It’s especially helpful for people transitioning from Windows x86, and for bridging from OSED it’s best to go through these things thoroughly once in advance.
But aside from that, I think the course content itself is already sufficiently detailed. Once you have the above foundations, just following the information and references in the course materials is usually enough to get things done. However, if your technical foundation is strong, you can try searching for 1-day vulnerabilities for the products listed in the syllabus and attempt to reproduce them yourself beforehand. The more sufficient your preparation before class, the better you can keep up with this very fast-paced course.
Overall, the course first explains from the more familiar Ring 3 perspective, then gradually shifts focus to the most mysterious part at Ring 0 the Windows Kernel for extremely challenging kernel exploitation. But my impression is that the course mainly focuses on Advanced Exploit Development in the Windows environment, rather than discovering vulnerabilities from a vast unknown structure.
- To quote the instructor:
- “Any single subsection of this course could take you a week of research; we will not over-focus on the ‘banging your head against the wall’ parts.”
In terms of exploit development, I think EXP-401 is truly top-tier. Because modern Windows systems have many mitigations, the course guides students step by step to understand the implementation of each mitigation and modern feasible bypass techniques, and on top of that, focuses on exploit stability.
In typical environments, people usually only focus on the exploitability and whether exploitation can succeed. However, EXP-401 places great emphasis on the exploit’s survivability across different environments, for example, an exploit that still runs stably on different versions. This sounds like black magic in the binary exploitation field, right? Every offset is a carefully calculated essential component, but EXP-401 disregards that aspect.
It even includes whether the program can be perfectly restored to its original state after the exploit finishes. In all situations, students are required to ensure the program runs stably after the exploit completes; crashes in the attacked program after executing the exploit are not accepted.
So rather than saying EXP-401 is a vulnerability-finding course, I think EXP-401 is actually more about teaching you how to conduct advanced exploit development implementing exploits that can survive in different environments and remain stealthy and undetected. To be honest, it has a bit of an APT flavor.
Interesting Investigation
I did some digging: as of 2024/6/21, there were 135 OSEE holders worldwide, and that’s the total since OSEE was first issued. Using the Wayback Machine to investigate, it seems the earliest issuance date of OSEE was around July 2009. If we calculate directly, on average only 9 OSEEs are certified per year, which shows just how extremely high the difficulty and rarity of this certification are.
 An average of only 9 OSEEs per year
An average of only 9 OSEEs per year
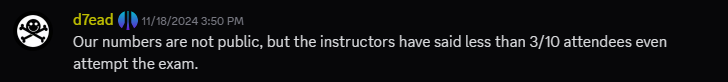
But that seems somewhat unreasonable. If a class has around 10+ people (our class had 7, which seems on the low side), and there’s one AWE training per month, then at least 120 people per year could take the exam. If so many attend the course, why are the pass numbers so low? With that question in mind, I continued wandering around the official Discord server until I found a message from OffSec staff in Discord general.
Turns out fewer than 3/10 of those who take the course actually take the exam. By the way, during the live training I even heard the instructor say the pass rate is only about 10%. Given the current pace of about 1.2 classes per month, perhaps this is reasonable…?
Estimating with averages, let’s say there were 140 OSEE holders at the start of 2025. But this year, the first group from Taiwan to challenge OSEE all passed! We had a total of 7 people almost covering the entire year’s volume. Adding the 9 people who appeared in the OSEE-masters channel on Discord, as of 2025/8/11 it’s roughly estimated that 16 people obtained OSEE this year. Our group directly pulled up the world’s average for this year by approximately 77.78%, so now there are probably only about 156 OSEE holders on the entire planet pretty interesting.
A Magical Journey
The Beginning of the Story
It was around September 2023. While routinely tidying up Gmail, I suddenly saw a very unusual email. The domain was from OffSec. Clicking it open, Cathy told me there would be an Advanced Windows Exploitation course around August 2024. My first thought was, oh! EXP-401 is actually being offered in Taiwan things just got interesting :)
In fact, long ago probably when I first encountered OffSec in high school I had heard of this course. My first impression was that it was a course of very high professionalism and difficulty, and its overall design happened to hit my aesthetic sweet spot.
To say I wasn’t tempted would be impossible. I remember the price being around 3000 or 4000 USD back then if I squeezed a bit, maybe I could take it.
Later I heard that DEVCORE and OffSec held four Live Training courses in Taipei: EXP-401, PEN-200, WEB-200, SOC-200. I heard the training method was to have OffSec’s academy instructors teach directly, which sounded very cool.
Time passed, and it came up again during a DEVCORE dinner gathering. Right, EXP-401 is offered in August. I rushed to check the DEVCORE Training official website. Hmm! At this price, forget it!
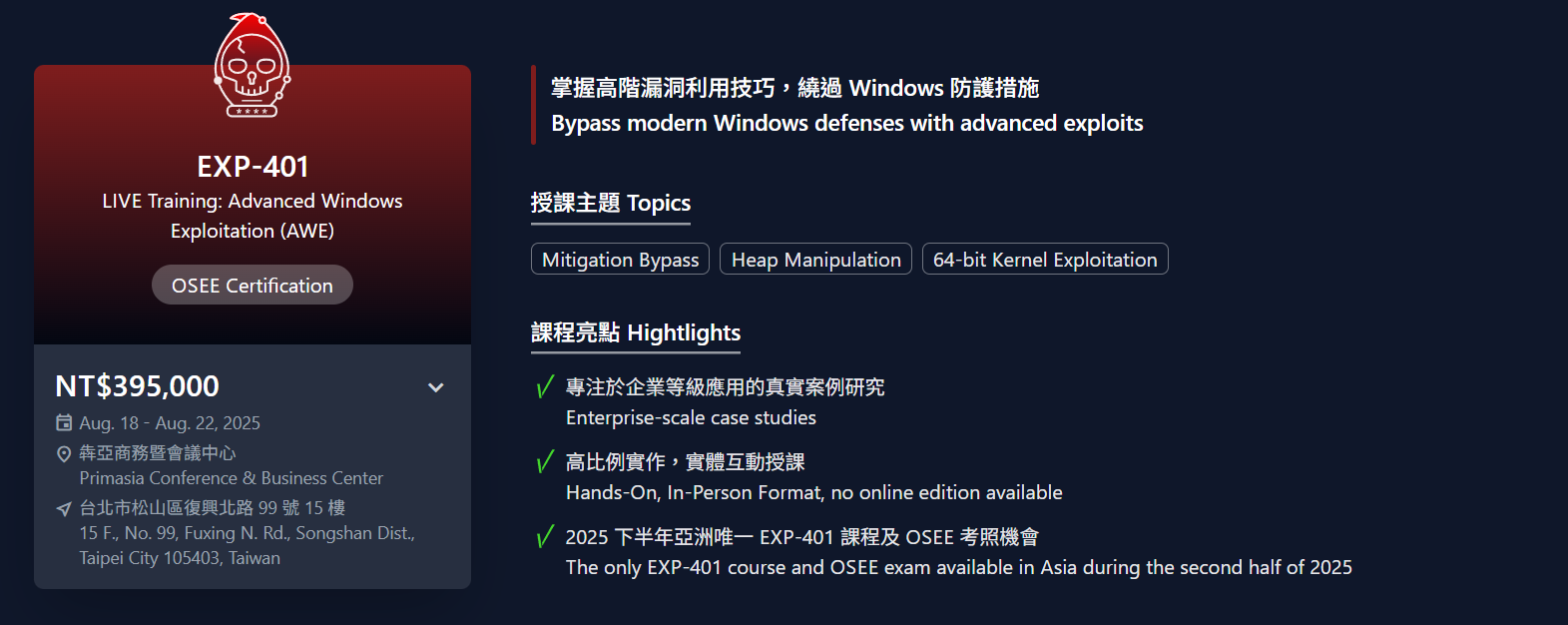 2025 EXP-401 price (back then it also seemed to be in the 400k+ TWD range 💀)
2025 EXP-401 price (back then it also seemed to be in the 400k+ TWD range 💀)
Yep, the hardest point came back to price. After all, I had just paid tuition then and was a super broke freshman. On the one hand, this was a rare opportunity to take EXP-401 in Taiwan; on the other hand, my savings were so miserable I could cry. I thought about this for a long time.
But then I seriously considered that if I missed this opportunity, who knows whether there would be another similar one. Usually you have to go to BlackHat to attend. This time it was in-country, and the organizers and the OffSec folks coming to Taiwan were people I knew. Considering the costs of traveling abroad airfare, accommodation, meals it might even be cheaper in Taiwan. Also, my home is just a little over 20 minutes from NTUT could I… live at home?
And honestly, this has always been my dream certification. If I achieved it, I would have completed a life goal.
Hmm! Grit my teeth and swipe the card!
Looking at my savings now destined for days of “eating dirt” and the successful registration email, I suddenly felt grateful I could live at home; otherwise, I’d literally starve outside 💀
Three days before class, I received the pre-departure notice email, including schedule info, minimum hardware requirements, pre-course recommended knowledge, etc. There were 20 pre-read links, each containing a massive amount of knowledge. Bro, even if you had sent them 20 days earlier, I might not have finished reading them all 💀
Since it was absolutely impossible to read everything, I first picked a few unfamiliar parts and searched using the keywords. The first slide deck Google found I clicked it and started reading. I thought, wow, I directly found a Chinese version of the slides how special. As I read, I realized the entire deck was in Traditional Chinese, and as I scrolled further, the style felt familiar…? I suddenly had a hunch and scrolled to the first page to see who made the slides.
It said “AngelBoy” in big letters. Bro, my classmate is literally the teaching material itself 💀
Day 1 - Shellcoding & VMware Workstation Internals
The course start date arrived quickly. Only today did I find out who my classmates were looking at the sign-in sheet, almost everyone was from the DEVCORE Research Team. The only two not from the Research Team were me and @Lays. The extreme excellence of my classmates made me feel pressured from the start 💀
Anyway,
EXP-401 Login
I was the first to enter the classroom. As soon as I walked in, the two instructors greeted me kindly. After a brief chat, I saw a super thick textbook lying on the desk. Picking it up, I could immediately feel the “dictionary-level” weight. Flipping through, I found the content very, very rich each chapter’s techniques had detailed explanations. If you’ve dealt with Windows, you know there are tons of complex structures; the book also carefully diagrammed the relationships of each structure, which is friendly for newcomers.
But after reading for a bit, I realized something was off. Do we really have time to finish all this?
- Me:
- Are we really going to finish all this in five days?
- Nasro:
- Usually we can’t, but we hope to :)
(shaking)
At the beginning of class, the instructors introduced the general process of the course and the challenges we would face over the next five days, and showed us the AWE WTF Level. You’ve probably seen this image online it’s accurate based on how it felt 💀
After all the introductions, the instructor gave us his blessing:
- Nasro:
- “I hope everyone can get enough sleep in the coming days ;)”
? Wait a second, what do you mean
Side note: I originally thought that since I was living at home, I could still get a full 8 hours of sleep. But in the following days, I averaged about 5 hours per night 💀
In the morning, the instructor first shared all course materials via USB. Then we began some basic knowledge lectures, such as x64 shellcode and DEP bypass. This period was likely to help EXP-401 students quickly get into the groove experience the course’s rhythm and get used to the instructors’ pace. I must say, the instructors taught extremely well in terms of pace and the difficulty of the English to me it felt very suitable for people who can read basic original documentation.
After finishing the morning basics, Nasro mentioned a little Easter egg about the WiFi on site.
- Nasro:
- Do you know why the WiFi password looks like that?
- Nasro:
- Because of Reverse Engineering (laughs)
Honestly, it was pretty funny w
In the afternoon, we moved on to some internal mechanisms of VMware Workstation as well as vulnerability triggering & exploitation. Near the end of the day, the instructor offered a bonus if anyone could stack a ROP chain to achieve a specific function, they would receive a Challenge Coin. But on the first day, due to “first-look environment kills” + super annoying debugging issues, no one could properly stack ROP to get the coin. After that, Orange said, “Three MSRC Top 100 can’t stack a single ROP,” which became a running joke for all five days XDDD
After class, I really felt that one monitor made things hard. Coincidentally, @terrynini felt the same. “Bro, go to Syntrend and buy a second monitor.”
The instructor then left a small challenge if anyone completed it, they’d get a mysterious gift. The first day ended peacefully. From how it felt, the first day had less pressure; the content to review and preview was still manageable, and I could even smoothly finish the small challenge.
Day 2 - VMware Workstation Escape & Microsoft Edge Internals
Morning another beautiful day. Sleeping at home fully restored my energy. Being able to sleep at home while taking EXP-401 is awesome, hehe.
I took the MRT to Zhongxiao Xinsheng, grabbed a coffee, and headed to NTUT felt like I was on vacation, chill.
Before class, I checked my answers with the instructor and passed the small challenge, so I got a cool EXP-401 sticker.
When we were about to start, I noticed @terrynini really brought a second monitor 💀
In the morning, we continued the previous day’s progress. After bypassing most mitigations, we successfully popped a meterpreter session on VMware Workstation. It was here that I truly felt the course’s pace growing more intense.
Everything seemed to be going smoothly! But Microsoft added many mitigations to Windows. While my brilliant classmate and the instructors discussed how to leverage the ROP we had just stacked to bypass a very tricky restriction, he suddenly posed a soul-searching question with a new bypass idea.
It seemed even the OffSec folks hadn’t considered it, and everyone suddenly fell silent, thinking about its feasibility.
- At that moment, Vixx said:
- “If you can do that, I’ll give you a challenge coin!”
I don’t know whether it eventually succeeded XD
In the afternoon, we moved into Microsoft Edge, covering most of its internal workings. After a few attempts, we achieved an Arbitrary Read Write Primitive. From here on out, you really need a lot of hands-on work to fully grasp the course knowledge. The instructor gave the class its first Extra Miles as homework complete it and you’d get a Challenge Coin.
I felt this was an Extra Mile I might be able to finish, so I sacrificed some sleep at night and got half of it done.
Day 3 - Microsoft Edge Browser Pwn & Sandbox Escape
Today’s course focused entirely on Edge. We quickly reviewed the exploitation chain from the start and applied multiple techniques to bypass mitigations. In the afternoon, we focused on the sandbox implementation, related operating structures, and how to leverage certain characteristics to escape the sandbox. At this point, cognitive load was about to explode.
We ended with a bit of Windows Kernel knowledge. Since I had previously played with the Windows Kernel, I had some foundation, so this part was okay. But then we got a Kernel Extra Miles.
I initially thought, “should be fine,” but opening it revealed an Extra Miles that filled two whole A4 pages. Bro, I’ll pass I need to sleep.
But yesterday’s Extra Mile seemed promising at half-done, so I spent extra time to finish it. The price of an Extra Mile is hair loss due to lack of sleep 💀
By the way, the afternoon tea every day was great here’s a box I particularly liked.
Day 4 - Windows Kernel Internals & Windows Kernel Exploitation
Early in the morning, I checked answers with Nasro and got the Challenge Coin. The EXP-401 coin looks awesome.
What’s special today is that OffSec was conducting interviews with students, and I happened to be one of the interviewees. I went to a mysterious little room upstairs and chatted with OffSec’s waytan for a bit. After the interview, I received a Kali Challenge Coin, and my number was the uniquely special 699.
 Kali Challenge Coin & EXP-401 Challenge Coin
Kali Challenge Coin & EXP-401 Challenge Coin
Starting today, we switched from Ring 3 to Ring 0 to explore the most mysterious part of Windows the kernel. In the morning, we learned a large amount of foundational Windows Kernel knowledge, including many kernel-specific mechanisms. In the afternoon, we focused on the implementation of mitigations and bypass techniques, and we successfully used a kernel driver to obtain SYSTEM.
A wonderful day ended. After a full day of high-intensity exploitation, it was time to treat ourselves. I met up with @StevenMeow and @MuMu, who was also in Live Training, to eat steak.
Day 5 - Usermode Callback & Kernel Mitigation Bypasses
Finally survived to the last day.
That’s right! Microsoft’s security team implemented many mitigations for the Windows Kernel. For ordinary users, this is well-intentioned, but for hackers in the modern 2025 exploitation environment, it’s a nightmare.
In addition to reliably triggering vulnerabilities, we also need to perform fancy bypasses for each mitigation. Back in the 19XX era before I was born, you could still execute shellcode on the stack. Now the stack is non-executable, and there are even more mitigations 💀
On the last day, we needed to bypass all mitigations and successfully exploit certain Windows Kernel characteristics to obtain EoP in the kernel. As time drew to a close, for some reason everyone got more hyped; in the last few chapters, we stood up watching WinDbg and IDA fly across the screen until the course ended.
All in all, I learned so much in these five days. I didn’t expect to survive so long in such a tense and exciting course. Cognitive load exploded. When I later read every piece of material, I realized how many details I initially didn’t understand. But it was truly a very fulfilling and challenging course.
About the Exam
Exam Preparation
If facing a formidable enemy requires going all out, then the perfect weapon must be prepared in advance.
Since OffSec exams allow up to four monitors, I used two 32:9 monitors + two 16:9 monitors. For the exam experience, having two 32:9 monitors is extremely, extremely convenient. If I needed to look up documentation, I could lay it all out on the top monitors; for writing the exploit, I’d use the left monitor; the center monitor was for debugging and reverse engineering; and the right monitor was just for the proctoring screen. Of course, the laptop in the middle absolutely can’t be there during the exam it’s just where I normally put it. After all, a touch screen is really handy XD
With hardware ready, next came some small supplies. Although EXP-401 is a 72-hour exam, for college students, pulling three all-nighters for finals is normal. So I prepared my finals week setup in advance: “Four cans of Monster.”
Plus the EXP-401 textbook, some notes, and a Challenge Coin as my amulet XD
With everything ready, it was time to begin. Having over-prepared for several months and equipped with my most familiar setup, I looked forward to facing this challenge well.
Exam Scheduling
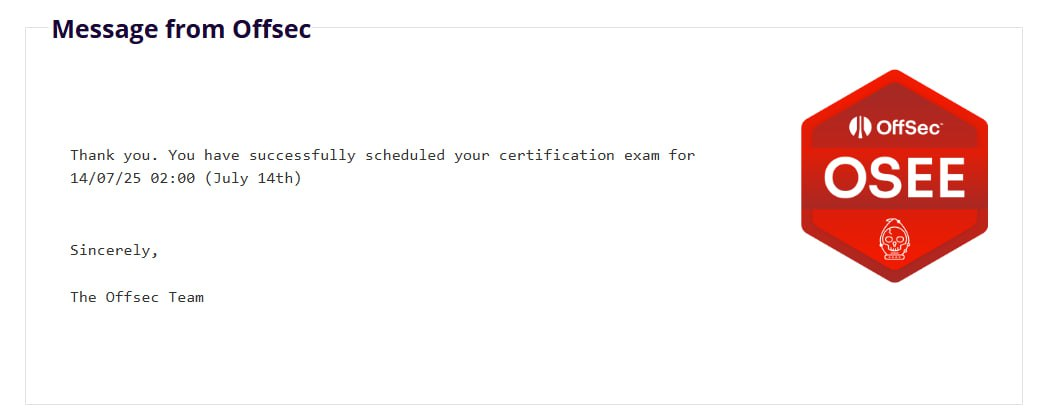
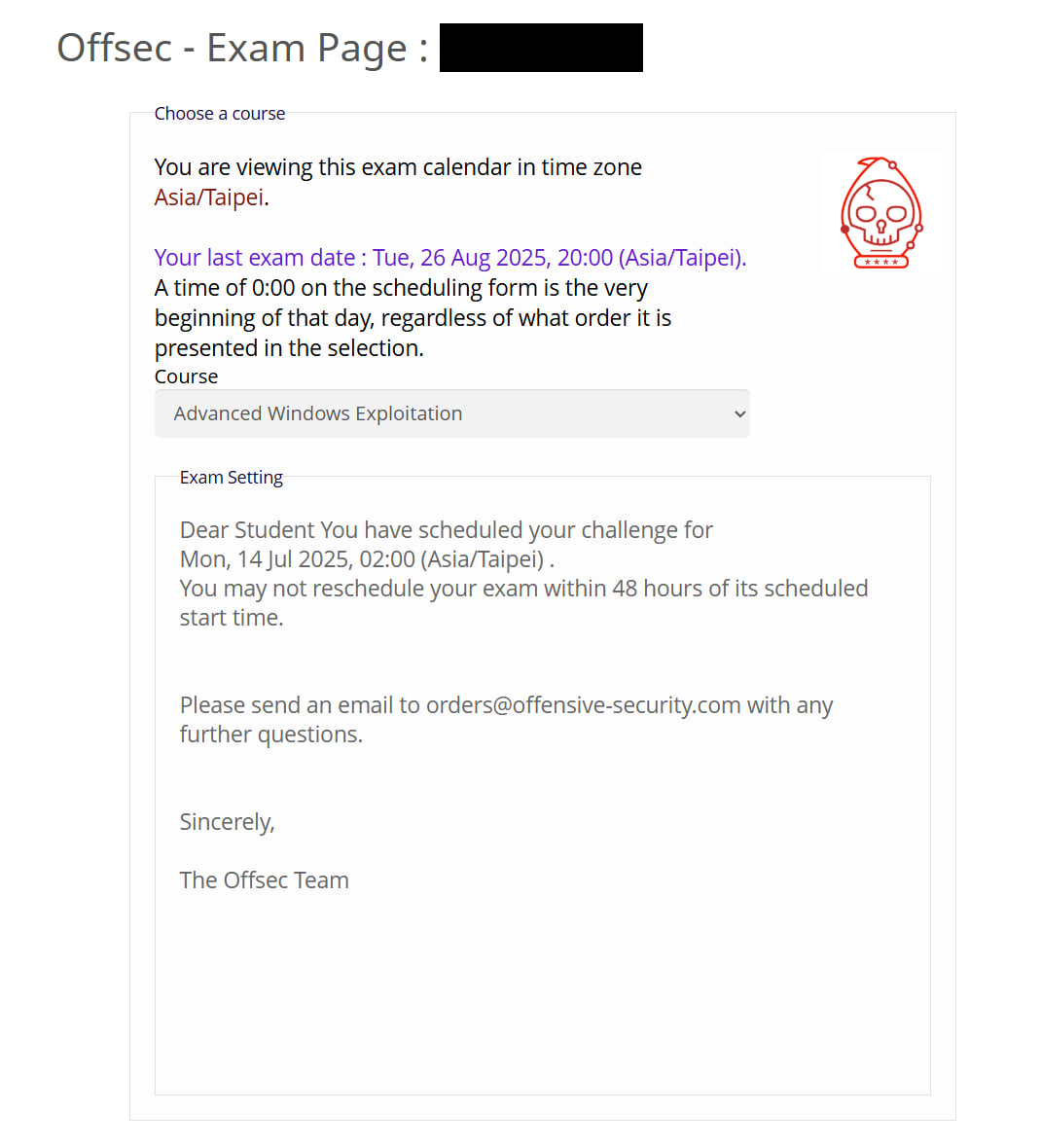
Around the end of March, OffSec suddenly updated EXP-401, including a new syllabus. The news exploded because no one knew if the exam would change accordingly. Since EXP-401 is taught with a physical textbook, if the course version changes, those without updated knowledge absolutely couldn’t take the exam. So recently, many people scheduled OSEE exams, and I quickly booked a time too. I originally planned to take it in early May, but at the end of April my mindset suddenly collapsed, so I delayed a bit before booking the exam.
Because so many were scheduling, the remaining exam slots were somewhat awkward. The only time in July was around 2 AM. Although taking an exam in the early morning is total jail time, it seemed to be the only slot, so I booked it.
Hmm! All set. With my usual “American schedule,” it should be fine! So I left it as is.
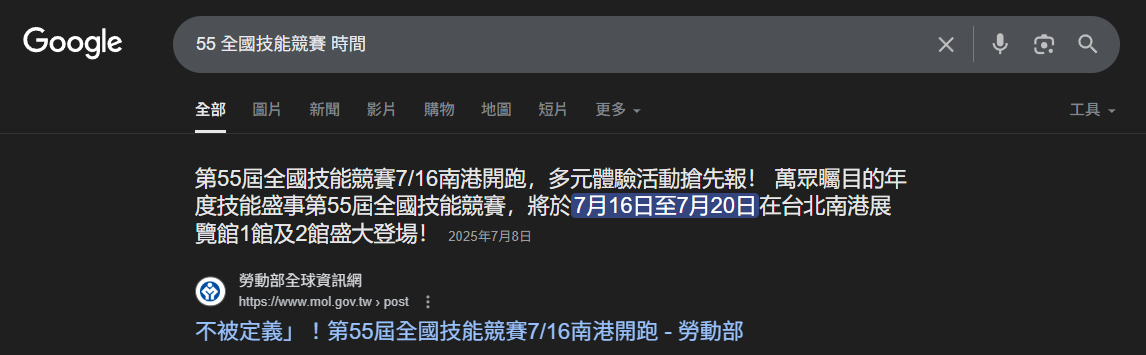
Just as I thought the only issue was the exam time, I suddenly remembered that mid-July was the National Skills Competition.
No way my OSEE is on 7/14 at 2:00 AM, but the competition starts on 7/16. If OSEE is 72 H + 24 H, it will definitely clash.
Yep, I almost forgot the National Skills Competition schedule. When I added it to my calendar, I found it was a perfect clash. My third and fourth days of the exam overlapped with the first and second days of the competition. It was 2025/07/10 at the time only 8/4 and 8/15 slots remained, but I really didn’t want to delay anymore. So I could only figure out how to take OSEE while competing in the national team selection 💀
I let it sit until two days before the exam too late to change time forcing myself to become Superman.
Exam Situation
For specific exam notes, see the OSEE Exam Guide, which includes everything you need to know.
Anyone who has taken an OffSec exam knows you can’t say much here, but I can describe how it felt to me.
Unlike previous exams, EXP-401’s exam is the only one that allows using LLMs. Whether it’s ChatGPT, Copilot, Gemini whatever it doesn’t matter, because I think the exam is something AI fundamentally cannot solve. Also, OSEE’s exam seems not to limit you to IDA Free or similar tool restrictions. In other words, under the rules, you could use Ghidra or IDA Pro during the exam. I don’t have IDA Pro, so I used IDA Free for the exam, but from the results, it didn’t seem to matter.
First, about the proctoring experience. The initial process was the usual verify identity, show the room, run scripts to test the computer setup, etc. But EXP-401’s proctoring felt peculiar. In terms of messaging, in prior exams, proctors would reply instantly when I messaged to take a break or asked questions. This time, the proctor felt less responsive if I said I was taking a break, they might reply one or two hours later, making me feel like a lovesick clown 🤡
But that’s understandable EXP-401 exams are quite rare. Perhaps EXP-401 is independent of other courses, and its uniqueness means the proctoring process is slightly outside the standard system (?)
Aside from that, there were no major issues. In fact, I felt more relaxed no one wants someone watching them for 72 hours, right?
Day 1 - Exam D-Day
Current time: 2025/07/14 AM 01:45:00. I chugged a can of Monster before the exam. It’s been two hours since I woke up feeling great, very alert.
After the usual identity verification, the exam began. Mine started at AM 02:00.
There are two challenges in total:
- User-Mode Exploitation
- Kernel-Mode Exploitation
I picked the more familiar Kernel first. As I read it, it didn’t seem too hard. One phase was very solvable at a glance I could tell how to handle it so I started writing a PoC and got over a small hump in just over an hour.
But after solving the first part, I got stuck at a strange point. After trying several times, there was no path forward. Perhaps there was another route. After a more fine-grained investigation and analysis, I found a second path and immediately grabbed 25 points.
2025/07/14 08:02:XX - Kernel-Mode Half Solved / 25 Point
With the big pit cleared, the rest wasn’t too hard. After ten minutes of PoC tweaks, I ran it on the target and completed the challenge.
2025/07/14 08:14:11 - Kernel-Mode Solved / 50 Point
At this point, it took about six hours to solve the Kernel part and get 50 points. Snagging half the points right off the bat gave me a lot of confidence, because the other one looked quite complex at first glance it made me wonder if I could really pull it off. But at least I still had plenty of time to analyze it slowly about 66 hours left, not much different from the start.
As I kept reading, I started to feel stuck. I tried several exploit combinations but they didn’t work no leads. Time for a break. I went to buy lunch and watched video while eating my double 4-ounce beef burger.
After lunch, I crashed hard on the bed. But after three hours, I suddenly woke up thinking of a place I might have missed. I got up, chugged another Monster, and looked back at the problem. I realized I had small mistake in the morning, causing the rest of the exploit process to collapse and wasting time on irrelevant things. After fixing it, I achieved a phased breakthrough and suddenly felt I could solve the mission.
I tried to string together the exploit chain I had considered in the morning. After a few experiments, it seemed promising and could bypass some annoying conditions. Later, refining the chain slowly, I finally achieved another big breakthrough after 23 hours of torment, bringing the total to 75 points.
2025/07/15 01:08:XX - User-Mode Half Solved / 75 Point
Day 2 - Exam Day & Report Day
I originally wanted to sleep after clearing a huge pit, but I couldn’t fall asleep in the chair my head was full of possible ways to chain the rest of the exploit. As I thought, I realized there might be a path, so I got up and continued.
Looking closely, the remaining parts might be simpler than I thought. After poking a few directions, I found some interesting characteristics. Based on that, I built a PoC and tried this approach; it worked and I got a breakthrough.
This time, the feasibility seemed especially high. I spent another 10 minutes adjusting the PoC. Feeling confident it would pass in one go, I fired it at the target machine. After a few seconds, I completed the second challenge and scored full marks on the OSEE exam.
2025/07/15 06:12:47 - User-Mode Solved / 100 Point
After getting full marks, I went straight to sleep. I passed out for three hours, then woke up and chugged another Monster to begin the subsequent report work.
What I did next was mainly:
- Reconstruct the entire exploitation process from the very beginning
- Divide the exploit chain into different obstacle-breaking phases
- Treat each obstacle as a chapter and explain it
- Describe the mechanism of each exploitation step as clearly as possible
- Take screenshots according to each exploitation phase
In short, the rest of the time was spent constantly taking screenshots and writing the report.
Day 3 - Report Day / National Team Selection Day 0
Then it was 2025/07/16. Yep! Today was competitor check-in day! I had to run to Nangang Exhibition Center to check in and then rush back home to continue the exam and I couldn’t be away too long or I wouldn’t finish the report! I hadn’t slept since waking up at 2 PM the previous day. After telling the proctor I was taking a long break, I showered and ate a meal that I wasn’t sure should count as breakfast or dinner, then got ready to head out. I thought I still didn’t feel sleepy and was somewhat energetic, but when I looked in the mirror, my face looked exactly like it does during NTUST finals week so funny.
A friend also happened to be participating in the National Skills Competition in the Graphic Design category, so his mom gave me a ride thank you, auntie QQ.
At check-in, I also saw @TwinkleStar and @nella, which was amusing. The situation was something like this:
- Me:
- Do we need to stay? I have to run.
- Star:
- Why
- Me:
- Because I’m taking OSEE right now
- Star:
- I can tell
LOL I must have looked like a dead person outside, which scared me into chugging another Monster.
At least the check-in was successful and I wasn’t disqualified!
After checking in, I rushed home for a quick shower. It was so hot outside that if you lay on the road, you’d be medium-rare in minutes I melted completely.
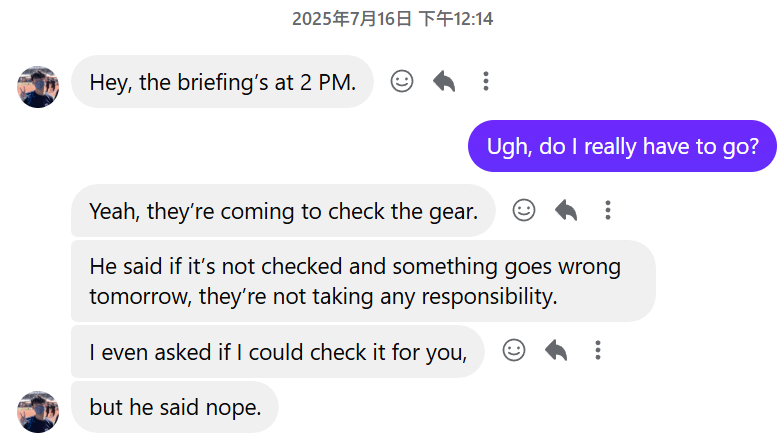
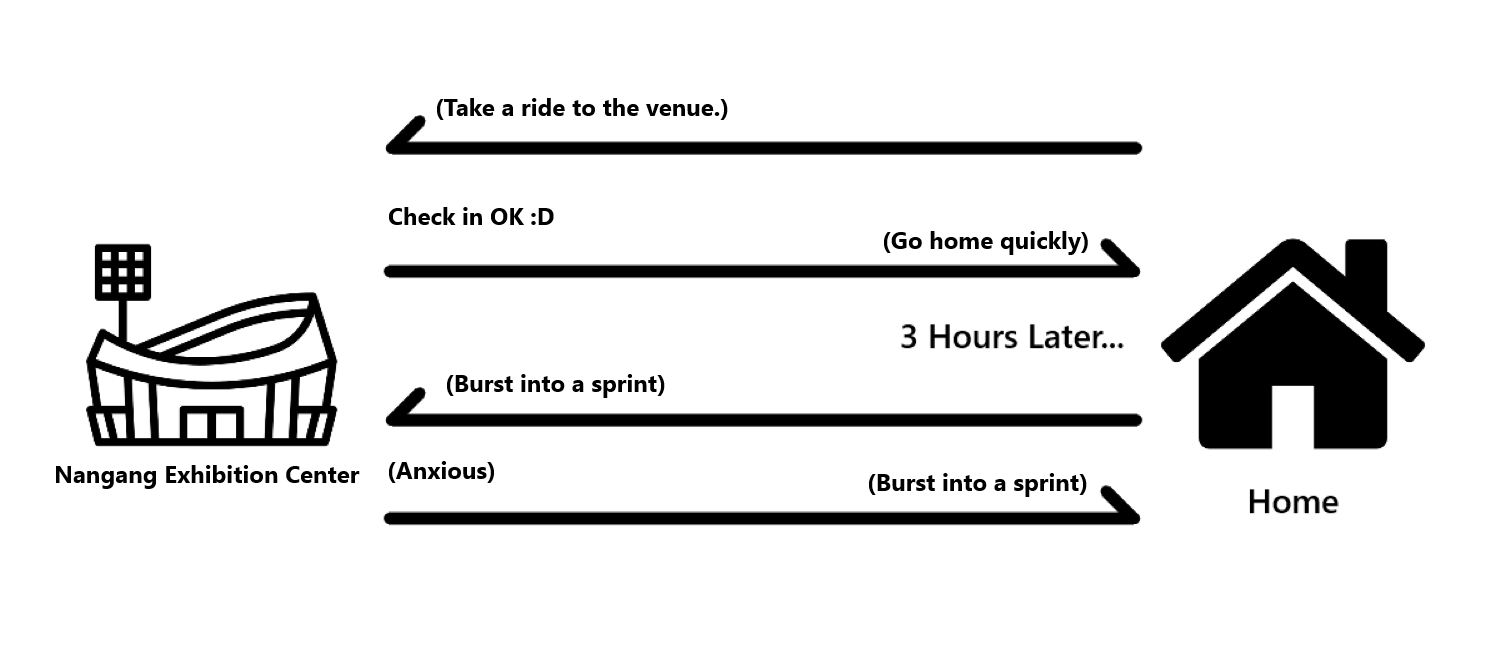
I thought I was free afterwards and continued to focus on the report for two hours. While stepping out of the room for a water break, I saw a message from my teammate.
Seriously? We also had to do equipment checks. Fine, I had to go. Luckily, I live close to the venue only 20 minutes away otherwise I would’ve broken down.
In short, here was my schedule on day three of the OSEE exam a total adrenaline rush.
After that, I tried to take the most complete and bulletproof set of screenshots possible, using images to represent relationships in parts that were hard to explain. And so it continued until Day 4.
Day 4 - Report Day / National Team Selection Day 1
At 2025/07/17 AM 1:45:00, the proctoring ended. What followed was the painful fine-tuning of the report. But don’t forget, I had to be at the National Team Selection at 8:00 AM, so I had to leave two hours to sleep; otherwise, I’d die at Nangang Exhibition Center.
So I had to sleep by around AM 5:10. After closing the report, I leaned back and immediately passed out after two sleepless days.
AM 7:20 sounds like time for an 8 AM class hell for normal college students, especially if you barely slept the day before. Worse still is being jarred awake after just two hours by an alarm.
Let’s summarize the current situation:
- A severely overworked college student
- Slept about 6 hours over three days
- Chugged four cans of Monster in three days
- A “final exam” starting in 40 minutes
- The “final” runs from 8:00 AM to 4:00 PM
- A massive final report due in 18 hours
Hmm? Sounds like an average NTUST finals week so it’s fine.
I struggled through half of the morning’s digital forensics. During lunch break, I ran to a place where no one could see me to write the report. In the afternoon, after solving half of the hardening tasks, I couldn’t hold on and passed out at the competition venue. Thanks to @tyc4d for holding the rest having reliable teammates is great 🫵😭
After it ended, I sprinted home from Gongguan MRT’s Ubike at max speed and continued endless writing. From the moment I got home until 20 minutes before the deadline, my hands didn’t stop. I had heard from @angelboy that someone failed because their report wasn’t detailed enough. So after submitting all FLAGS, I spent about three full days meticulously writing a very detailed report.
Every diagram had frames marking the meaning and targets of each memory address; every structure member was clearly defined; the entire exploit chain was perfectly explained ensuring the report was beyond reproach. If that still feels unreal, the rigor was: 182 pages and 22,000 words I’m basically a novelist.
Halfway through, an emergency occurred. Due to four days of intense stress + severe sleep deprivation, my vision started to blur.
Struggling with “Minecraft nausea debuff” eyes for two hours, another emergency hit.
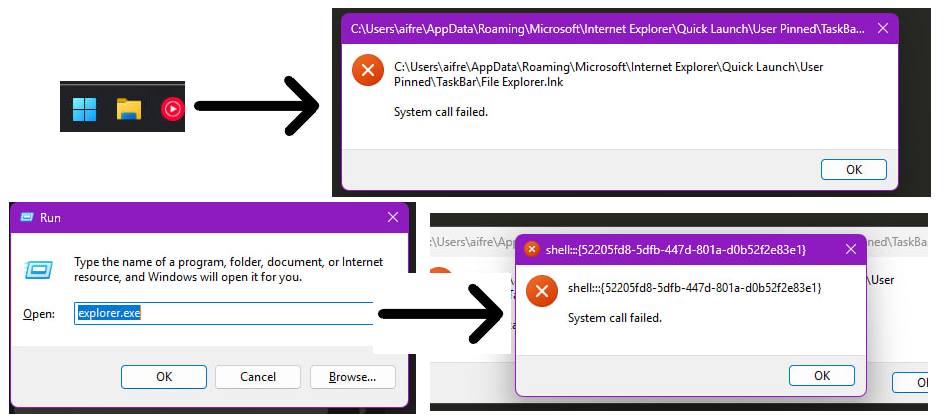
Clicking the Explorer icon instantly popped “System call failed.” Running explorer.exe via Win + R also caused “System call failed.” Bro, I didn’t even touch you why are you screaming?
It was around 12:00, with 1 hour and 45 minutes left before the report deadline. If my system died, I would be completely unable to submit my report. I felt that rebooting would certainly kill the system, so I could only grit my teeth and keep writing.
My hands never stopped writing until 20 minutes remained. After finishing the last page, I immediately saved as PDF and carefully checked each page for completeness. Once confirmed, I packaged the files according to the OSEE Exam Guide submission format and uploaded them to OffSec’s submission platform end of round.
Now it was 2025/7/18 AM 1:36:XX 9 minutes left before the deadline. It felt like
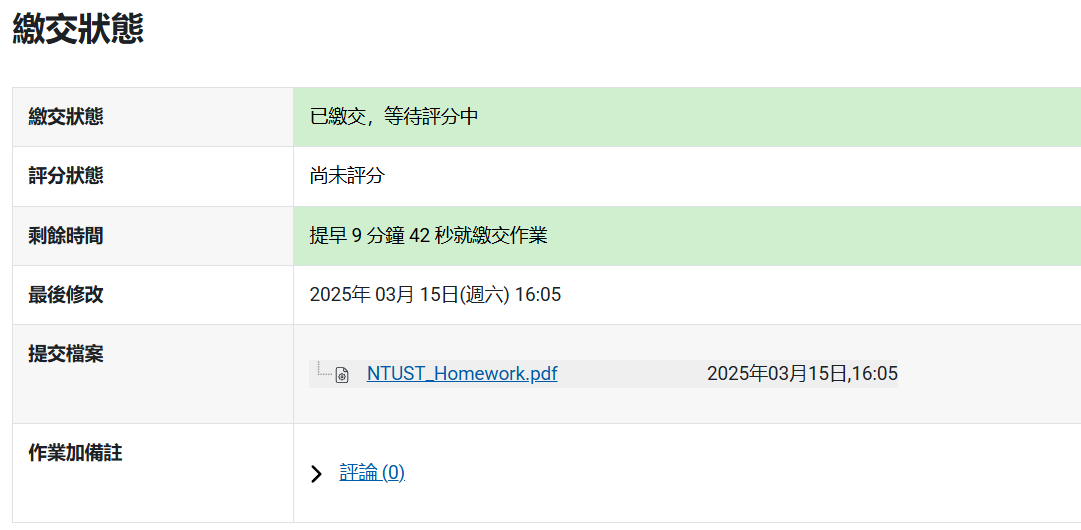 Submitted the assignment 9 minutes and 42 seconds early
Submitted the assignment 9 minutes and 42 seconds early
Exam Result
After submission came the extremely long wait. Usually OffSec certification results never take more than three days, but I waited almost 10 days with no result, and there were three others in the EXP-401 Discord channel also waiting.
After reading a few blogs, I found that EXP-401 exam reports seem to be reviewed only by EXP-401 instructors, separate from OffSec’s certification committee. Since they’re busy, long waits are normal 💀
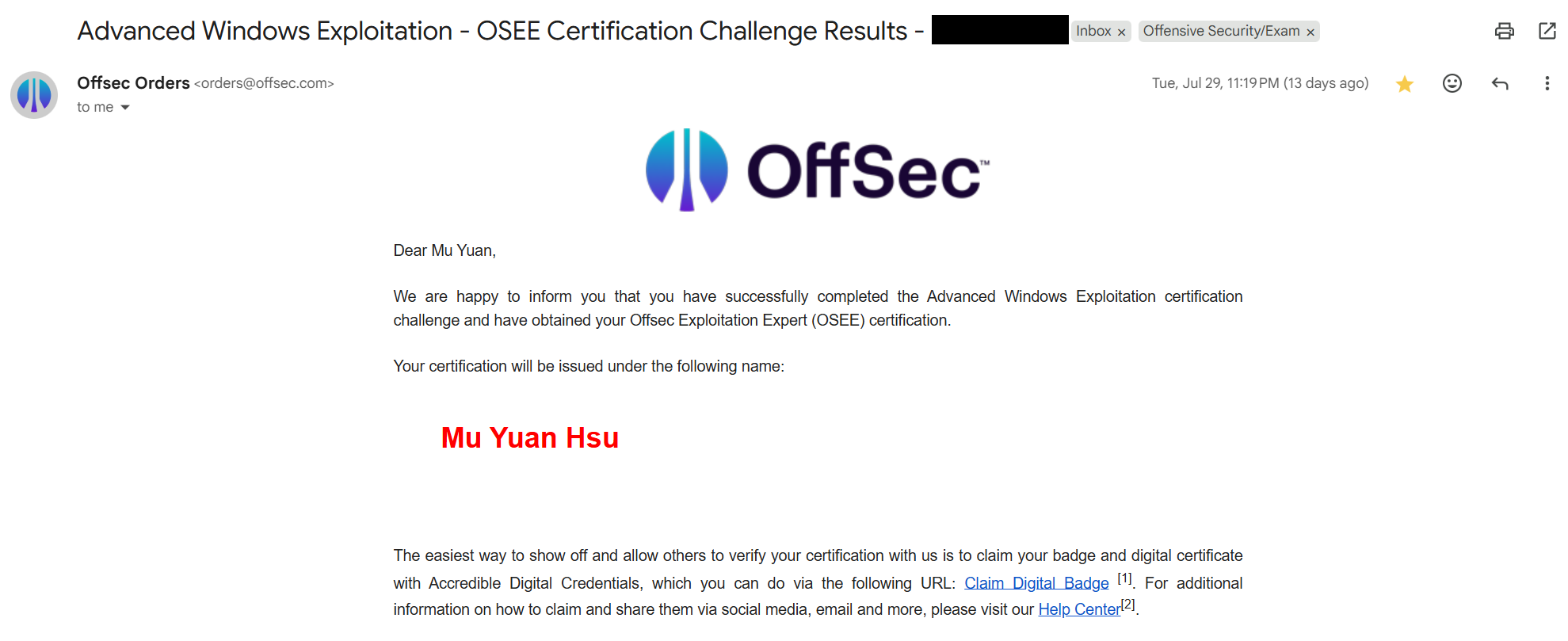
After a long wait, I finally received the pass email. I was TA’ing at AIS3 at the time; I couldn’t hide my happiness and got caught, LOL. But I still wanted to hold it in and post a big blog after AIS3 ended hehe.
Becoming an OSEE felt complicated part severe imposter syndrome, part disbelief that I became one of the world’s few OSEE holders. I had always considered obtaining the top certification my dream, but once achieved, I had these complex feelings so strange XD
In short, I achieved one of my life goals. Perhaps this won’t be the end, but it’s definitely a perfect end to a chapter.
 Offensive Security Exploitation Expert - OSEE
Offensive Security Exploitation Expert - OSEE
Conclusion
I can only say the process of this exam was too exciting not writing a blog would be impossible.
Because I bought the Learn Unlimited Subscription back in high school, I’ve taken almost all OffSec courses. I can assure you EXP-401 is the most different OffSec course I’ve taken the difficulty, pace, and exam are all very unique.
Especially regarding difficulty, I feel the gap from the 300 level is enormous. Honestly, going from 200 to 300 felt like crossing just a threshold before, but touching EXP-401 was shocking. If 200 to 300 is like going from elementary to middle school, then 300 to 400 is like jumping from middle school straight to a Master’s degree the gulf in difficulty is tremendous.
Since I currently have the Learn Enterprise Subscription, I can say without exaggeration that after reading EXP-401, going back to EXP-301, my first impression was that those materials would only fill about 30 pages (plus a bit) if placed in EXP-401. Basically, EXP-401 is entirely built on a complete understanding of EXP-301 just like PEN-300 is an extension built on a complete understanding of PEN-200.
For those who want to better understand modern Windows high-level attack methods, including kernel-level ones, or who are passionate about pursuing technical excellence, I highly recommend EXP-401. I believe it will bring far more gains than expected this is the best course I’ve taken.
By the way, I accidentally made it into the top three of the National Team Selection and advanced to phase two. Taking OSEE while competing was pure torture.
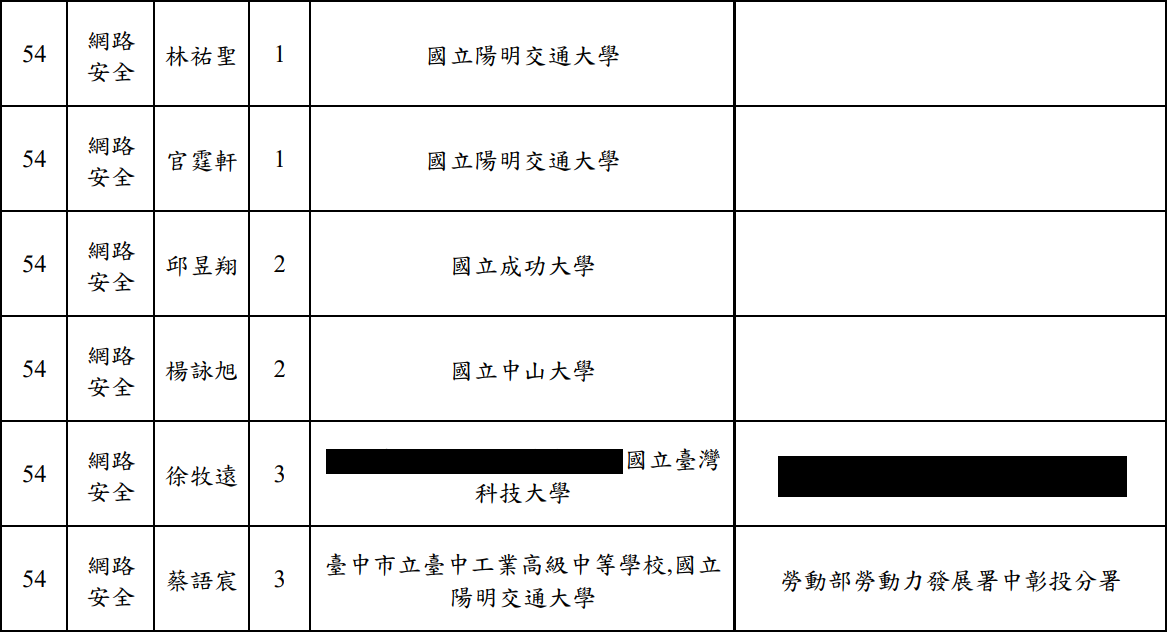 Made it to phase two of the national team selection
Made it to phase two of the national team selection
Thoughts on the Class
I usually took OffSec courses online. Trying Harder in person this time was a completely different experience. Almost everyone in the class was a friend already seen in the community; the overall vibe felt more like a community meetup especially in Taiwan’s unique environment XD. Interestingly, I heard we were the only group that could fully keep up with the entire course.
I used to learn from web pages or PDFs. What’s special about EXP-401 is that only the physical original book is available. Reading halfway and looking back at the pages I’d turned gave me a sense of “oh! I finally got here,” and I could directly feel the weight of knowledge.
In this EXP-401 Live Training, the seven of us were Taiwan’s first cohort to receive the training, and we were also the smallest class of all. Counting other classes after dismissal, they seemed to have 15+ people; the PEN-200 OSCP class even seemed to have nearly 30. But our EXP-401 class had only seven and except for the godly Lays, all were DEVCORE powerhouses. I thought it would be intensely stressful in such a class, but in practice it was super hype, not the cold and tense atmosphere I imagined XD
I was fortunate to participate in this Live Training held in Taiwan. For students, flying abroad just to take a course is not easy. In many people’s blogs, the first line is “Took a flight to XXX today, traveled to XXX or checked in at the hotel, and got ready for the torture of the next few days,” but my situation was “Wow, I can sleep at home! It’s even shorter than my commute to NTUST.” Very magical. Also, because of this, I had great sleep quality in those days no need to deal with jet lag or additional expenses. I could even have home-cooked dinners. Overall, it’s very suitable for those who don’t want to travel and have limited budgets.
Over these five days, I truly learned a lot. I didn’t expect to survive so long in such a tense and exciting course. I also deeply realized how far I am from the world’s most advanced research whether in exploitation thinking or the pursuit of perfect full-chain exploits this course gave me so much.
Finally, I tried chaining everything together from Edge Browser Pwn inside VMware, then escaping VMware Workstation while doing Process Hollowing, and then using the host’s Windows Kernel for EoP to obtain a SYSTEM-privileged meterpreter shell.
When “meterpreter session 1 open!” appeared in my multi-handler, an indescribable feeling emerged from my heart a sense of fulfillment and an excitement beyond words.
Three years ago, when I first executed shellcode on the stack to get a reverse shell, I could never have imagined that three years later, I would only need to browse a webpage in Microsoft Edge inside a VM to perform Browser Pwn, VMware Guest-To-Host escape, and Windows Kernel exploitation all the way to a stable meterpreter shell. Honestly, it’s not only growth along the way, but also a precious experience earned through countless nights of hard work.
Even if this could be seen as merely reproducing exploits, understanding all the principles, reversing Windows Kernel, Edge, and VMware, and obtaining a meterpreter shell from an exploit I wrote myself this feeling is unparalleled.
But if that were all, it would be too simple. So I rebuilt a brand-new environment from scratch. Perhaps we can Try Harder turn Windows Defender fully on, and like an APT, burn through a dozen CVEs to break through all the way to the host.
If someone asks what you can do after learning EXP-401, it’s probably something like this:
Although the screen shows a lot of things flying around obviously someone is in the visual flair was kept for viewing pleasure, hehe.
Exam Reflections
I originally thought the OSEE exam would be an extremely difficult journey, but actually taking it felt like only about 50% ~ 60% of the textbook’s difficulty. If you thoroughly digest the course materials before taking the exam, it feels like everything is under control.
In the end, I spent 28 hours to get a perfect 100, which surprised me. I honestly thought it would take at least two days to reach the passing line. Perhaps I’m continuously improving. Compared to a year ago, I’ve indeed grown a lot. I’m slowly becoming aware that I’m moving forward but the awkward part is not knowing where I stand now. Maybe I’m at the peak of the Dunning-Kruger effect without realizing it.
Looking back, the exam problems were indeed challenging and very well designed. I don’t think OSEE is as easy as some reviews claim. It’s not an exam you pass easily; it’s a gift for those who prepared diligently.
After finishing, I could feel the exam was just verifying whether you possess the concrete knowledge thoroughly explained in the textbook. OffSec’s materials love to include references at extendable points for you to read on your own, and those parts aren’t tested in OSEE. I believe only after reading all the references and practicing the knowledge on top of them can you truly be worthy of OSEE’s “top-tier certification” title.
EXP-401 may help someone who wants to become a researcher move closer to the world’s cutting-edge research, but to surpass OSEE-level abilities as NiNi mentioned in a blog “No certification can directly prove the quality of a person’s research. Real capability needs to be proven by accumulated achievements and published results.”
After every OffSec certification, I have the same feeling: the certification can provide a direction forward, but once you reach the end, you always find it was only the starting point. Continuing down the road beyond that is stepping into uncharted, deepest territory.
In short, there is too much to say about this course. Thanks to the comrades who fought alongside me for five days, constantly breaking the boundaries set by OffSec in those painful hours. Thanks also to DEVCORE and OffSec for providing such a good learning environment and resources. I look forward to the day I can touch the skyline of top-tier research.
 EXP-401 / Advanced Windows Exploitation - Completed
EXP-401 / Advanced Windows Exploitation - Completed
If you want to prepare for EXP-401, I hope what you’ve read here helps.
Quoting what Gustave from Expedition 33 said:
For those who come after.
Gustave , Clair Obscur: Expedition 33
Here’s a song I listened to often while reading EXP-401: